Using Ethernet to communicate
From IGEP - ISEE Wiki

|
In this guide is used IGEP firmware Yocto |
Contents
Overview
You can log into IGEP via many interfaces, such Serial, Wifi, USB-Ethernet Gadget, etc. In this tutorial we are going to connect to the board via its Ethernet interface. By default, all IGEP Processor boards have a static IP in their Ethernet interface which is 192.168.5.1 and dynamic IP address assigned via DHCP.
Requirements
There are some requisites to follow this guide:
- IGEP Processor Board with Ethernet
- Host PC
Configure Host PC
IGEP Dynamic IP
Connect to IGEP device
Now you are ready to log into IGEP via its Ethernet interface. You just need a program with a SSH client.
In this tutorial we are going to use Putty, as it is a multi-platform program.
You can download it from its official page at:
http://www.chiark.greenend.org.uk/~sgtatham/putty/download.html
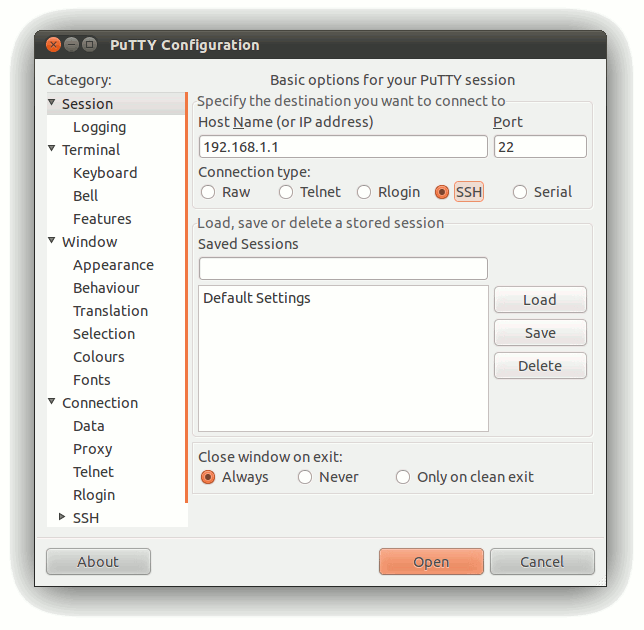
Install and run Putty. It will look like this:
Follow these steps to connect to IGEP:
- Select the SSH at connection type.
- Insert the IP address of the target (IGEP default IP: 192.168.5.1)
- Ensure that the port is set to 22, the default for SSH communications.
- Finally, press the Open button to start the SSH session.
If everything goes right, you will be able to access to an IGEP console from your PC via Ethernet.
To login IGEP use:
user:root password: (no password for this user: press return)
Troubleshooting
WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED!
In the case of the SSH client in Linux, a changed host key results in the client refusing to connect and showing an remote host identification has changed error
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ @ WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED! @ @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ IT IS POSSIBLE THAT SOMEONE IS DOING SOMETHING NASTY! Someone could be eavesdropping on you right now (man-in-the-middle attack)! It is also possible that the RSA host key has just been changed. The fingerprint for the RSA key sent by the remote host is 8d:0b:29:f0:0a:a1:f5:56:0c:12:18:b0:26:02:6d:9d. Please contact your system administrator. Add correct host key in /home/eballetbo/.ssh/known_hosts to get rid of this message. Offending key in /home/eballetbo/.ssh/known_hosts:57 RSA host key for 192.168.7.1 has changed and you have requested strict checking.
To fix the problem edit your ~/.ssh/known_hosts and remove the line corresponding to this host.